NEW! Download Gartner® Report: Use RAG as a Service to Boost Your AI-Ready Data. Get Started.




NEW! Download Gartner® Report: Use RAG as a Service to Boost Your AI-Ready Data. Get Started.




NEW! Download Gartner® Report: Use RAG as a Service to Boost Your AI-Ready Data. Get Started.





What is Encryption?
What is Encryption?
What is Encryption?
October 25, 2020
October 25, 2020
What is encryption?
What is encryption?
Securing sensitive data using encryption is a cornerstone of cybersecurity. Does your vendor encrypt data in transit, at rest and in use?
Securing sensitive data using encryption is a cornerstone of cybersecurity. Does your vendor encrypt data in transit, at rest and in use?
On September 27, 2020, Universal Health Services, one of the largest healthcare providers in the United States, was hit by a ransomware attack, disrupting service and compromising patient confidence. Earlier that same month, a woman in Düsseldorf, Germany, died because a ransomware attack prevented doctors from accessing critical data during her medical emergency. Doctors transferred the woman — and other patients — to another facility, but the delay led to her death.
These two examples underscore the real cost of data breaches, which extends far beyond financial and reputational risks. Enterprises that require a mission critical level of support — enterprises like healthcare, financial services and government — must do everything in their power to secure their networks and data. One way we help them do this is with encryption.
These two examples underscore the real cost of data breaches, which extends far beyond financial and reputational risks. Enterprises that require a mission critical level of support — enterprises like healthcare, financial services and government — must do everything in their power to secure their networks and data. One way we help them do this is with encryption.
On September 27, 2020, Universal Health Services, one of the largest healthcare providers in the United States, was hit by a ransomware attack, disrupting service and compromising patient confidence. Earlier that same month, a woman in Düsseldorf, Germany, died because a ransomware attack prevented doctors from accessing critical data during her medical emergency. Doctors transferred the woman — and other patients — to another facility, but the delay led to her death.
On September 27, 2020, Universal Health Services, one of the largest healthcare providers in the United States, was hit by a ransomware attack, disrupting service and compromising patient confidence. Earlier that same month, a woman in Düsseldorf, Germany, died because a ransomware attack prevented doctors from accessing critical data during her medical emergency. Doctors transferred the woman — and other patients — to another facility, but the delay led to her death.
Healthcare “Financially motivated criminal groups continue to target this industry via ransomware attacks. Lost and stolen assets also remain a problem in our incident dataset. Basic human error is alive and well in this vertical. Misdelivery grabbed the top spot among Error action types, while internal Misuse has decreased.”
Healthcare “Financially motivated criminal groups continue to target this industry via ransomware attacks. Lost and stolen assets also remain a problem in our incident dataset. Basic human error is alive and well in this vertical. Misdelivery grabbed the top spot among Error action types, while internal Misuse has decreased.”
https://www.healthcareitnews.com/news/uhs-says-all-us-facilities-affected-apparent-ransomware-attack
https://www.healthcareitnews.com/news/uhs-says-all-us-facilities-affected-apparent-ransomware-attack
Financial Services & Insurance: “The attacks in this sector are perpetrated by external actors who are financially motivated to get easily monetized data (63%), internal financially motivated actors (18%) and internal actors committing errors (9%).”
Financial Services & Insurance: “The attacks in this sector are perpetrated by external actors who are financially motivated to get easily monetized data (63%), internal financially motivated actors (18%) and internal actors committing errors (9%).”
https://www.healthcareitnews.com/news/hospital-ransomware-attack-leads-fatality-after-causing-delay-care
https://www.healthcareitnews.com/news/hospital-ransomware-attack-leads-fatality-after-causing-delay-care
Public Administration (Government): “Ransomware is a large problem for this sector, with financially motivated attackers utilizing it to target a wide array of government entities. Misdelivery and Misconfiguration errors also persist in this sector.”
Public Administration (Government): “Ransomware is a large problem for this sector, with financially motivated attackers utilizing it to target a wide array of government entities. Misdelivery and Misconfiguration errors also persist in this sector.”
https://enterprise.verizon.com/resources/reports/dbir/2020/data-breach-statistics-by-industry/healthcare-data-breaches-security/
https://enterprise.verizon.com/resources/reports/dbir/2020/data-breach-statistics-by-industry/healthcare-data-breaches-security/
The recommendations of the DBIR report include identifying and encrypting sensitive information. How exactly does that work? Let’s start by defining encryption.
The recommendations of the DBIR report include identifying and encrypting sensitive information. How exactly does that work? Let’s start by defining encryption.
Before we take a closer look at encryption, it will help to better understand the data breach landscape. Every year, Verizon publishes the Data Breach Investigation Report (DBIR). The 2020 DBIR analyzes 3,950 confirmed data breaches and summarizes the threats facing three key industries this way:
Before we take a closer look at encryption, it will help to better understand the data breach landscape. Every year, Verizon publishes the Data Breach Investigation Report (DBIR). The 2020 DBIR analyzes 3,950 confirmed data breaches and summarizes the threats facing three key industries this way:
Data Breaches by Industry
Data Breaches by Industry
What is Encryption?
What is Encryption?
Types of Encryption
Types of Encryption
Technically speaking, encryption converts plaintext to ciphertext. To put it more simply, encryption scrambles readable data and only authorized users can unscramble it to read it. Data is encrypted using a mathematical algorithm that relies on encryption keys that are typically randomly generated. Decrypting the data (reversing the process from ciphertext to plain text) also requires an encryption key.
Encryption protects data, securing it so that unauthorized readers can’t steal it — in the case of a data breach or malware infection — or accidentally leak it — in the case of human error.
Encryption protects data, securing it so that unauthorized readers can’t steal it — in the case of a data breach or malware infection — or accidentally leak it — in the case of human error.
There are two main types of encryption: symmetric (or private key) encryption and asymmetric (or public key) encryption. Symmetric encryption uses the same key to encrypt and decrypt data. Asymmetric encryption uses one key for encryption and a different key for decryption. One isn’t necessarily better than the other, they each serve different purposes and offer different advantages.
There are two main types of encryption: symmetric (or private key) encryption and asymmetric (or public key) encryption. Symmetric encryption uses the same key to encrypt and decrypt data. Asymmetric encryption uses one key for encryption and a different key for decryption. One isn’t necessarily better than the other, they each serve different purposes and offer different advantages.
Secure Sockets Layer (SSL) and Transport Layer Security (TLS), SSL’s successor, use asymmetric encryption. SSL and TLS both encrypt data at rest — in storage —and in transit — while it’s moving from one server to another — and SearchBlox supports both.
Secure Sockets Layer (SSL) and Transport Layer Security (TLS), SSL’s successor, use asymmetric encryption. SSL and TLS both encrypt data at rest — in storage —and in transit — while it’s moving from one server to another — and SearchBlox supports both.
“We can secure any data source when using ElasticSearch,” explains Selvaraj. “And because we support OpenSSL, TLS 1.2/13 and AES-256, we enable you to meet stringent security standards and compliance requirements.” Those include:
“We can secure any data source when using ElasticSearch,” explains Selvaraj. “And because we support OpenSSL, TLS 1.2/13 and AES-256, we enable you to meet stringent security standards and compliance requirements.” Those include:
Health Insurance Portability and Accountability Act (HIPAA)
Payment Card Industry (PCI) Data Security Standard
National Institute of Standards and Technology (NIST) Security Framework
Health Insurance Portability and Accountability Act (HIPAA)
Payment Card Industry (PCI) Data Security Standard
National Institute of Standards and Technology (NIST) Security Framework
“Our Platinum Support data privacy module enables you to search data while it’s still protected with AES-256 encryption,” explains Timo Selvaraj, SearchBlox’s co-founder and VP of product management. This “searchable encryption” is a game changer for enterprises: Every user can search the data, but only privileged users can see the decrypted Personally Identifiable Information (PII).
“Our Platinum Support data privacy module enables you to search data while it’s still protected with AES-256 encryption,” explains Timo Selvaraj, SearchBlox’s co-founder and VP of product management. This “searchable encryption” is a game changer for enterprises: Every user can search the data, but only privileged users can see the decrypted Personally Identifiable Information (PII).
And while SSL and TLS protect data in transit and at rest, AES-256 protects data in use. AES stands for Advanced Encryption Standard. The 256 refers to a key length of 256 bits, which makes the key virtually unbreakable with existing computer power. AES-256 requires the same key that was used to encrypt the data to decrypt it. In other words, it uses symmetric encryption.
And while SSL and TLS protect data in transit and at rest, AES-256 protects data in use. AES stands for Advanced Encryption Standard. The 256 refers to a key length of 256 bits, which makes the key virtually unbreakable with existing computer power. AES-256 requires the same key that was used to encrypt the data to decrypt it. In other words, it uses symmetric encryption.
Technically speaking, encryption converts plaintext to ciphertext. To put it more simply, encryption scrambles readable data and only authorized users can unscramble it to read it. Data is encrypted using a mathematical algorithm that relies on encryption keys that are typically randomly generated. Decrypting the data (reversing the process from ciphertext to plain text) also requires an encryption key.
Technically speaking, encryption converts plaintext to ciphertext. To put it more simply, encryption scrambles readable data and only authorized users can unscramble it to read it. Data is encrypted using a mathematical algorithm that relies on encryption keys that are typically randomly generated. Decrypting the data (reversing the process from ciphertext to plain text) also requires an encryption key.
SearchBlox’s Single-Click Data Encryption
SearchBlox’s Single-Click Data Encryption
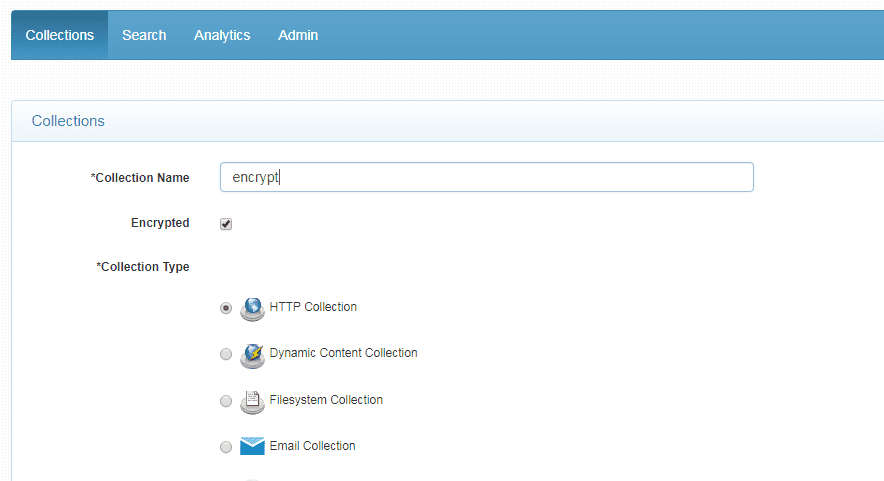


Encrypt your data instantly.
Encrypt your data instantly.
SearchBlox 9.2 supports the encryption of content and specific metadata fields.
Limiting access to PII is crucial, but your data does you no good if it’s locked away in silos. We enable you to encrypt columns of content and meta fields within a data record so you can protect sensitive PII, while still making data searchable and accessible to authorized users. And you can do it all with a single click once you’ve created and classified sensitive users.
Limiting access to PII is crucial, but your data does you no good if it’s locked away in silos. We enable you to encrypt columns of content and meta fields within a data record so you can protect sensitive PII, while still making data searchable and accessible to authorized users. And you can do it all with a single click once you’ve created and classified sensitive users.
In addition to searchable encryption, Platinum Support offers emergency patches and hot fixes, so you also get a one-hour response time and faster issue resolution.
In addition to searchable encryption, Platinum Support offers emergency patches and hot fixes, so you also get a one-hour response time and faster issue resolution.
Protect your data — and your reputation.
Protect your data — and your reputation.
Protect your data — and your reputation.
To learn more about single-click data encryption, take a look at our developer support. To explore searchable encryption, view our Platinum Support page, which includes pricing.
To learn more about single-click data encryption, take a look at our developer support. To explore searchable encryption, view our Platinum Support page, which includes pricing.

Enhance your users’ digital experience.
We build AI-driven software to help organizations leverage their unstructured and structured data for operational success.
4870 Sadler Road, Suite 300, Glen Allen, VA 23060 sales@searchblox.com | (866) 933-3626





Still learning about AI? See our comprehensive Enterprise Search RAG 101, ChatBot 101 and AI Agents 101 guides.
©2025 SearchBlox Software, Inc. All rights reserved.
Enhance your users’ digital experience.
We build AI-driven software to help organizations leverage their unstructured and structured data for operational success.
4870 Sadler Road, Suite 300, Glen Allen, VA 23060 sales@searchblox.com | (866) 933-3626





Still learning about AI? See our comprehensive Enterprise Search RAG 101, ChatBot 101 and AI Agents 101 guides.
©2025 SearchBlox Software, Inc. All rights reserved.
Enhance your users’ digital experience.
We build AI-driven software to help organizations leverage their unstructured and structured data for operational success.
4870 Sadler Road, Suite 300, Glen Allen, VA 23060 sales@searchblox.com | (866) 933-3626





Still learning about AI? See our comprehensive Enterprise Search RAG 101, ChatBot 101 and AI Agents 101 guides.
©2024 SearchBlox Software, Inc. All rights reserved.




